Pegasus Spyware
- Yaniv Hoffman
- Aug 19, 2023
- 18 min read
Pegasus is a highly sophisticated spyware tool developed by the Israeli cyber arms firm, NSO Group. The spyware is designed to target mobile devices, such as smartphones, and is capable of infecting both iOS and Android operating systems.
Once a device is infected with Pegasus (either by clicking a malicious link or by technique called zero click), the spyware delivers a chain of zero-day exploits to penetrate security features on the phone and installs Pegasus without the user’s knowledge or permission. Once the phone is exploited and Pegasus is installed, it begins contacting the operator’s command and control (C&C) servers to receive and execute operators’ commands, and send back the target’s private data, including passwords, contact lists, calendar events, text messages, and live voice calls from popular mobile messaging apps. The operator can even turn on the phone’s camera and microphone to capture activity in the phone’s vicinity.
– From min 1:09
Scary ahhaaa? But that’s only the beginning. This spyware is extremely sophisticated and modular, in addition to allowing customization. It uses strong encryption to protect itself from detection by traditional security tools and has a vigorous monitoring and self-destruct mechanism. Lookout’s analysis determined that the malware exploits three zero-day vulnerabilities, Trident, in Apple’s iOS which I want to explain on each bit . now I will explain later on the new vulnerabilities from 2020 and 2021 but first lets start from 2016 where it started
1. CVE-2016-4657: Memory Corruption in Safari WebKit
A memory corruption vulnerability exists in Safari WebKit that allows an attacker to execute arbitrary code. Pegasus ex- ploits this vulnerability to obtain initial code execution privileges within the context of the Safari web browser.
This vulnerability is complex and Lookout continues to work on analyzing this vulnerability and will publish additional findings as they become available.
2. CVE-2016-4655: Kernel Information Leak Circumvents KASLR
Before Pegasus can execute its jailbreak, it must determine where the kernel is located in memory. Kernel Address Space Layout Randomization (KASLR) makes this task difficult by mapping the kernel into different and unpredictable locations in memory. In short, before attacking the kernel, Pegasus has to find it.
The attacker has found a way to locate the kernel by using a function call that leaks a non-obfuscated kernel memory address in the return value, allowing the kernel’s actual memory location to be mapped.
3. CVE-2016-4656: Memory Corruption in Kernel leads to Jailbreak
The third vulnerability in Pegasus’ Trident is the one that is used to jailbreak the phone. A memory corruption vulnerability inthekernelisusedtocorruptmemoryinboththe32-and64-bitversions. Theexploitsareperformeddifferentlyon each version.
This vulnerability is complex and Lookout continues to work on analyzing this vulnerability and will publish additional findings as they become available.

While the spyware is sophisticated, the attack is very simple in its delivery and also silent in delivering its payload. The attack starts when the attacker sends a website URL (through SMS, email, social media, or any other message) to an identified target. The user only has to take one action--click on the link. Once the user clicks the link, the software silently carries out a series of exploits against the victim’s device to remotely jailbreak it so that the espionage software packages can be installed. The user’s only indication that anything happened will be that the browser closes after the link is clicked.
The espionage software contains malicious code, processes, and apps that are used to spy, collect data, and report back what the user does on the device. This spyware can access and exfiltrate messages, calls, emails, logs, and more from apps including What’s App, Gmail, Facebook, Line, Facetime, We chat, calendar, skype telegram, Kakakao talk and more [Maybe here put on screen logo of these apps]
In order to accomplish this, the spyware, once it jailbreaks the user’s phone, does not download malicious versions of these apps to the victim’s device in order to capture data, rather it compromises the original apps already installed on the device. This includes pre-installed apps such as Facetime and Calendar and those from the official App Store.
Usually, iOS security mechanisms prevent normal apps from spying on each other, but spying “hooks” can be installed on a jailbroken device. Pegasus takes advantage of both the remote jailbreak exploit and a technique called “hooking.” The hooking is accomplished by inserting Pegasus’ dynamic libraries into the legitimate processes running on the device. These dynamic libraries can be used to hook the apps using a framework called Cydia Mobile Substrate, known to the iOS jailbreak community, and which Pegasus uses as part of the exploit.
BTW, In later versions of Pegasus, user doesn’t need even to click a link as Pegasus uses a technique called “Zero click exploitation” and its enough to send a message or call the phone to infect it. but we will talk more about it later
But before we get more into the technical details of Pegasus, lets speak briefly about it origins.
So as I mention at the beginning, Pegasus was developed by the Israeli cyber arms firm, NSO Group, which was founded in 2010.
The company is known for developing advanced spyware and surveillance tools that are sold to governments and law enforcement agencies around the world.
The origins of Pegasus can be traced back to a project called "The Cyber Weapons Arms Race," which was launched by NSO Group in the early 2010s. The goal of the project was to develop advanced spyware tools that could be used for intelligence gathering and law enforcement purposes. Pegasus was one of the tools that was developed as part of this project.
Pegasus was first discovered in 2016, when it was used to target a human rights activist in the United Arab Emirates. Since then, it has been linked to a number of high-profile incidents, including the targeting of journalists and political opponents in several countries
On 18 July 2021, The Pegasus Project (a collaboration between journalists from 17 media organizations in 10 countries coordinated by Forbidden Stories, a Paris-based media non-profit, with the technical support of Amnesty International) reported that they obtained over 50,000 phone numbers of potential targets of the clients of the NSO group, an Israeli Technology firm. The list includes journalists, activists, academics, lawyers, politicians/ government officials, businessmen, doctors, prosecutors and friends and relatives of apparent people of interest for NSO clients.
BTW, there is a great book telling that story, written by Laurent Richard & Sandrine Riguad. Here is the book which I will leave also link in the description for those of you that are interested to learn more.
Who are the main customers of Pegasus worldwide?
Citizen lab of Toronto University that researched Pegasus extensively developed a scanning technique to identify Pegasus operation and Between August 2016 and August 2018, they detected 1,091 IP addresses and 1,014 domain names matching their fingerprint. Using this method they identified 36 distinct Pegasus systems, each one perhaps run by a separate operator.
In more details Citizen lab used the technique that they call Athena to cluster the IP addresses that matched our Pegasus fingerprints into what we believe are 36 distinct operators; each operator makes use of multiple IP addresses. They gave each operator an Operator Name drawn from national symbols or geographic features of the country or region that appears to be targeted. For each IP address used by the operator, They extracted a domain name from its TLS certificate. Then they coded the domain names to generate a Suspected Country Focus and assessed whether there were Political Themes in the domains, which might suggest politically motivated targeting. Following it they performed DNS cache probing to generate a list of countries in which there are Possible Infections associated with the operator. [ While I speak about it, so all figures below]
Operators in America:

Operators in Africa:

Operators in Europe:

Operators in Middle East:

Operators in ASIA:


Amnesty international that like Citizen labs researched Pegasus, identified 11 countries with 50K phone numbers on the spy list also published their own map of infection.
Regardless of the diff of the lists, it is clear to say that the infection is cross countries with major risk on privacy.
Yet, like always lets also look at some examples allegedly related to Pegasus.
one is the case of Jamal Khashoggi. Khashoggi was a Saudi Arabian journalist who was critical of the Saudi government and its policies. In October 2018, Khashoggi was killed inside the Saudi Arabian consulate in Istanbul, Turkey. It is widely believed that the Saudi government was behind his murder.
– From 1:35 until 2:15 or 2:15 until 2:35 exactly on it
In July 2021, it was reported that Pegasus had been used to target Khashoggi's fiancée, Hatice Cengiz, both before and after Khashoggi's murder. According to the reports, Cengiz's phone was infected with Pegasus in September 2018, just weeks before Khashoggi's murder. The spyware remained on her phone until at least February 2019, and was used to monitor her communications and movements.
BTW, NSO denied the claims that their technology was associated in any way with Khashoggi murder

Another example that I would like to review more thoroughly is of Pegasus being used to target individuals is the case of Ahmed Mansoor, a human rights activist from the United Arab Emirates (UAE).
In August 2016, it was reported that Mansoor's phone had been infected with Pegasus spyware. The spyware was able to monitor Mansoor's calls, messages, emails, and location data.
The attack on Mansoor was particularly sophisticated, involving multiple zero-day vulnerabilities that were used to bypass the security features of his phone.
On the morning of August 10, 2016, Mansoor received an SMS text message that appeared suspicious. The next day he received a second, similar text. The messages promised “new secrets” about detainees tortured in UAE prisons, and contained a hyperlink to an unfamiliar website. The messages arrived on Mansoor’s iPhone 6 running iOS 9.3.3.

As soon as he got the messages, Mansoor forward it to Citizen labs (Cybersecurity group in University of Toronto) that recognized the links and claimed in their investigation that the domain name webadv.co belongs to a network of domains that they believe to be part of an exploit infrastructure provided by NSO Group
The way they did it is interesting, bit technical so hope you can follow:
The links sent to Mansoor used the domain sms.webadv.co. During the forensic investigation they identified a network of 237 live IP addresses included 52.8.153.44, to which sms.webadv.co resolves, and which returns an SSL certificate for *.webadv.co. The 237 IPs also included 52.8.52.166(aalaan.tv) and 162.209.103.68 (manoraonline.net), which were the two C2 servers in the spyware used in targeting Mansoor.
However, the 237 IPs and related domain names that mapped did not provide insight into the identity of the threat actor. The IP addresses all appeared to be associated with cloud VPS providers, which gave no clue as to the identities of the operators, and the WHOIS information was mostly private. Yet Citizen lab did note that several domain names had WHOIS registrants based in Israel (e.g., thainews.asia, kenyasms.org).
So they examined historical scanning data to see whether they could attribute the 237 IPs to a threat actor. They noted that at least 19 of these IPs had previously returned a different distinctive Google redirect in response to a “GET /”.
\xef\xbb\xbf<HTML><HEAD><META HTTP-EQUIV="refresh" CONTENT="0;URL=http://www.google.com/">\r\n<TITLE></TITLE></HEAD><BODY>\r\n</BODY></HTML>Figure 16 : Response to an HTTP GET exhibited by 19 IPs in historical scanning data (note that the first three bytes represent the unicode byte order mark — BOM).
These 19 IPs included an IP address that (later) resolved to manoraonline.net, one of the C2 servers for the spyware sent to Mansoor.
They then searched the same historical data for other IP addresses that matched this same fingerprint. Overall, between October 2013 and September 2014, they identified 83 IPs that matched the fingerprint. We found several IPs of particular interest. The IP address 82.80.202.200 matched the fingerprint from October 2013 until April 2014.
HTTP/1.1 200 OKContent-Type: text/htmlLast-Modified: Tue, 04 Jun 2013 15:28:04 GMTAccept-Ranges: bytesETag: "09a91b3861ce1:0"Server: Microsoft-IIS/7.5Date: Mon, 28 Oct 2013 21:23:12 GMTConnection: closeContent-Length: 127\xef\xbb\xbf<HTML><HEAD><META HTTP-EQUIV="refresh" CONTENT="0;URL=http://www.google.com/"><TITLE></TITLE></HEAD><BODY></BODY></HTML>The domain name qaintqa.com pointed to this IP address at the same time (from April 2013 to April 2016), according to DomainTools. The registrant information for this domain is:
Registrant Street: Medinat Hayehudim 85Registrant City: hertzliyaRegistrant State/Province: centralRegistrant Postal Code: 46766Registrant Country: ILRegistrant Phone: 972542228649Registrant Email: lidorg@nsogroup.comThey also found two other IP addresses of interest that matched the fingerprint: 82.80.202.204 and 54.251.49.214 matched the fingerprint in March 2014. The former was pointed to by mail1.nsogroup.com from 2014-09-24 to 2015-05-06 (PassiveTotal), the latter was pointed to by nsoqa.com from 2015-09-01 until present (DomainTools). Both domains are registered to NSO Group.
Given these findings, Citizen lab strongly suspected the network of domain names we uncovered was part of an exploit infrastructure for NSO Group’s mobile spyware
But what else can we say about Pegasus ?
So again , I go to Citizen Lab that has released a report detailing sophisticated iPhone exploits being used against nine Bahraini activists.
The activists were reportedly hacked with the NSO Group’s Pegasus spyware using two zero-click iMessage exploits:
· Kismet, which was identified in 2020 was launched against devices running at least iOS 13.5.1 and 13.7. It was likely not effective against the iOS 14 update in September
· and ForcedEntry, a newer vulnerability that was identified in 2021 that allegedly NSO Group started deploying the zero-click exploit that managed to circumvent BlastDoor, which Citizen Lab calls ForcedEntry. Amnesty Tech, a global collective of digital rights advocates and security researchers, also observed zero-click iMessage exploit activity during this period and referred to it as Megalodon.
BTW, Zero-click attacks are labeled as sophisticated threats because unlike typical malware, they do not require user interaction to infect a device. The latter zero-click spyware is particularly notable because it can bypass security protections such as BlastDoor, which was designed by Apple to protect users against zero-click intrusions such as these.
Mechanisms of Hacking
I would like to provide a high-level overview of the mechanisms by which the Bahraini targets were hacked and involves synthesis of data from multiple phones, including phones belonging to non-Bahraini targets.
July – September 2020: KISMET iMessage Zero-Click
When the KISMET exploit was being fired at one of the devices running iOS 13.5.1, the log showed crashes associated with IMTranscoderAgent, which is responsible for transcoding and previewing images in iMessages. Specifically, the crashes were segfaults in the com.apple.IMTranscoderPreviewGenerationQueue thread while apparently parsing color profile data in a JPEG image received via iMessage. [You can mark those on figure 6]

Figure 6: A symbolicated crash summary for KISMET on an iPhone Xs running iOS 13.5.1.
After the crashes, IMTranscoderAgent then invoked WebKit to download and render items from the Pegasus infection server. The rendering triggered a memory pressure warning (Health of your memory in system) in JavaScriptCore, and also triggered a Metal shader compilation (Metal Performance Shaders is a highly optimized library of graphics functions that can help application developers achieve great performance at the same time decrease work on maintaining GPU family specific functions. It provides functions including: Image filtering algorithms. Neural network processing)
September 2020: Back to One-Click Exploits
Shortly after one of the victims upgraded to iOS 14 in September 2020, they received an SMS link to Pegasus from “MailExpress,” indicating that the KISMET exploit was not supported on iOS 14.

Figure 7: Pegasus SMS message that victim received in September 2020 after updating to iOS 14.
The message was a fake DHL package tracking notification. The victim may have accidentally previewed the link in the message while attempting to copy the message to send it to citizen lab.
The victim VPN recorded that the link in the message was opened, and redirected to a unique subdomain api1r3f4.redirectweburl[.]com, allegedly a Pegasus link connected to the Bahraini government operator of Pegasus, LULU. BTW, This action did not result in the infection of the phone; it is possible that the target closed the preview before the exploit ran.
February – July 2021: FORCEDENTRY iMessage Zero-Click
Starting in February 2021, Citizen lab began to observe NSO Group deploying a new zero-click iMessage exploit that circumvented Apple’s BlastDoor feature. They referred to the exploit as FORCEDENTRY, because of its ability to circumvent BlastDoor.
Amnesty Tech also observed zero-click iMessage exploitation activity around the same time, and referred to the activity they observed as “Megalodon.” We confirmed with Amnesty Tech that the “Megalodon” activity they observed matches the characteristics of the FORCEDENTRY exploit that we observed.
When the FORCEDENTRY exploit was being fired at a device, the device logs showed crashes associated with IMTranscoderAgent. The crashes appeared to be segfaults generated by invoking the copyGifFromPath:toDestinationPath:error function on files received via iMessage.
The crashes appeared to be of two types:
1. Type one crashes indicate that the chain of events set off by invoking copyGifFromPath:toDestinationPath:error ultimately crashed while apparently invoking ImageIO’s functionality for rendering Adobe Photoshop PSD data.
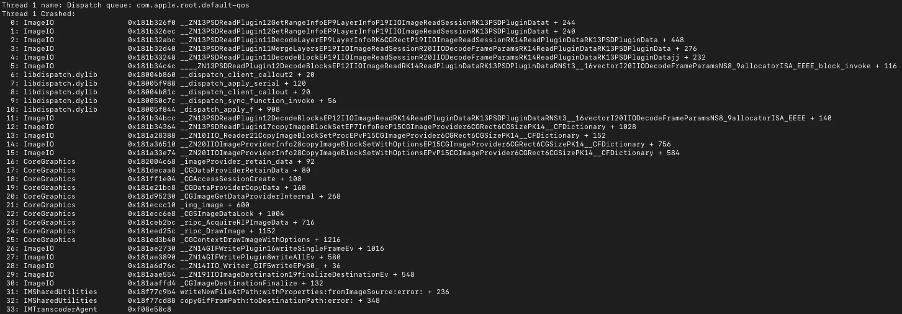
Figure 8: A Symbolicated Type One crash for FORCEDENTRY on an iPhone 12 Pro Max running iOS 14.6.
2. Type two crashes indicate that the chain of events set off by invoking copyGifFromPath:toDestinationPath:error ultimately crashed while invoking CoreGraphics’ functionality for decoding JBIG2-encoded data in a PDF file.

Figure 9: A Symbolicated Type Two crash for FORCEDENTRY on an iPhone 12 Pro Max running iOS 14.6.
After the IMTranscoderAgent crashes, Citizen lab noticed that the Apple thermal monitoring daemon, thermalmonitord, returned a series of errors:
Exception caught during decoding of reply to message ‘propertiesOfPath:handler:’, dropping incoming message and calling failure block.
Then, thermalmonitord invoked the tailspin process three times. The tailspin process caused two segfaults, but we ultimately found an invocation of tailspin running alongside the spyware:
/usr/bin/tailspin test-symbolicate 1234567
Phone logs indicated that the “responsible process” for the spyware was amfid, the Apple mobile file integrity daemon.
We saw the FORCEDENTRY exploit successfully deployed against iOS versions 14.4 and 14.6 as a zero-day.
With the consent of targets, we shared these crash logs and some additional phone logs relating to KISMET and FORCEDENTRY with Apple, Inc., which confirmed they were investigating.
Now, if you are still with me (I hope)…… there were hacks of course and I will leave the link for the report in description, so you can read in your own time.
Having said that, I MUST show the following: According to Citizen lab report, NSO Group has occasionally made use of visible decoy pages, perhaps in an effort to make their Pegasus infrastructure appear as innocuous servers.
The researchers found an interesting server, start-anew[.]net, which displayed an open directory listing that contained a decoy page.

Figure 11: How start-anew[.]net looked in a web browser.The directory contained a file, 1, which contained HTML source code for a website maintenance decoy page. The page was entitled “While maintenance:” and contained the text “Working hard to create a new website design. Stay in touch!”

Figure 12: How the decoy page (1) looks in a browser.
The title “While maintenance:” and the text “Working hard to create a new website design. Stay in touch!” exactly matched pages returned by two Pegasus servers that matched a fingerprint researchers used in their Hide and Seek report. These two servers were part of a group of Pegasus servers that were spun up in 2018 after Amnesty Tech and Citizen Lab published reports about the targeting of an Amnesty International staffer with Pegasus, but before Citizen Lab’s Hide and Seek report.
IP
Domain
Dates Matching Decoy Page
Dates Matching Hide and Seek Fingerprint
209.250.237.55
youneedjelly[.]net
8/28/2018 – 10/14/2018
8/31/2018 – 9/6/2018
92.222.71.144
visiblereminder[.]net
8/28/2018 – 9/11/2018
8/31/2018 – 9/6/2018
From the contents of start-anew[.]net, the researchers surmised that the following websites were part of the new Pegasus infrastructure:
· reunionlove[.]net
· news-now[.]co
· helpusfind[.]biz
One more interesting thing is that the researchers noted that these three domains were hosted on shared web hosting providers. In other words, the IP addresses that they pointed to had dozens of other innocuous domains also pointing to them. In previous iterations of NSO
Before I speak about the future of such spywares, for those of you that are interested to dive into more technical stuff like Pegasus code structure and main functions, techniques and ways of operation, I will leave the detail report of Lookout in the video descriptions so you could download it and look it by yourself and get your impression and view.
[Scroll down from page 14 and ahead to show tables of code]
The future of Pegasus and other similar spyware tools is uncertain, but it is likely that they will continue to evolve and adapt to new security measures and detection methods. Here are some potential developments in the spyware market and what they may mean for cyber security:
· Increased demand for spyware: With the rise of cybercrime, state-sponsored espionage, and surveillance, the demand for spyware is likely to increase. This may lead to the development of new and more sophisticated tools like Pegasus, as well as increased competition among vendors.
· Use of artificial intelligence and machine learning: As spyware becomes more complex, vendors may turn to artificial intelligence and machine learning to improve their products. This could include the use of AI to evade detection or to target specific individuals more effectively.
· Greater regulation and oversight: The use of spyware like Pegasus has raised significant ethical and legal concerns, and there is growing pressure on governments and the industry to regulate the use and sale of these tools. This may lead to greater oversight of the industry, as well as restrictions on the sale and use of spyware.
· Development of new detection and prevention tools: As spyware becomes more advanced, new detection and prevention tools will need to be developed to keep pace. This could include the use of machine learning to detect anomalies in network traffic, or the development of new anti-virus software that can detect and remove advanced spyware.
· Increased awareness and education: As the threat of spyware becomes more widespread, there is a need for greater awareness and education among the public and organizations. This may involve training programs for employees on how to identify and prevent spyware infections, as well as public awareness campaigns on the risks of state-sponsored espionage and surveillance.
To Summarize:
· Pegasus is a sophisticated spyware tool developed by NSO Group, which is capable of infecting mobile devices and stealing sensitive information.
· Pegasus has been used to target a wide range of individuals and groups, including journalists, activists, and government officials, often with the goal of suppressing dissent or uncovering sensitive information.
· Pegasus works by exploiting vulnerabilities in mobile devices, such as zero-day vulnerabilities, and can be delivered through various means, including phishing emails and text messages.
· Detecting and preventing Pegasus infections can be challenging, but there are steps individuals and organizations can take to protect themselves, such as keeping devices and software up to date, using anti-virus software, and avoiding suspicious links and attachments.
· The future of Pegasus and other spyware tools is uncertain, but it is likely that they will continue to evolve and adapt to new security measures and detection methods. This highlights the need for greater regulation, oversight, and education in the industry, as well as the development of new detection and prevention tools.
APPENDIX
Pegasus has also been the subject of significant controversy and debate in recent years. The spyware has been linked to a number of high-profile incidents, including the targeting of a journalist and human rights activist in Saudi Arabia, and the surveillance of political opponents in Hungary. The use of Pegasus raises serious ethical and legal concerns about privacy and human rights, and has led to calls for greater regulation of the cyber arms industry.
In summary, Pegasus is a highly advanced and controversial spyware tool that has significant implications for cybersecurity, privacy, and human rights. Its use highlights the need for greater transparency and accountability in the development and use of cyber weapons, and underscores the importance of strong cybersecurity measures to protect against these types of threats.
Can you technically explain how Pegasus works?
NSO Group has stated that Pegasus is intended to be used for legitimate law enforcement and intelligence purposes, such as investigating terrorism and organized crime. However, the use of Pegasus has raised significant ethical and legal concerns, particularly in cases where it has been used to target individuals who are not involved in criminal or terrorist activities.
Overall, the origins of Pegasus can be traced back to NSO Group's focus on developing advanced cyber weapons for intelligence and law enforcement purposes. While the original purpose of Pegasus may have been legitimate, its use has raised significant concerns about privacy and human rights, and has sparked a debate about the regulation of the cyber arms industry.
Journalists: In July 2021, a consortium of news organizations reported that Pegasus had been used to target journalists around the world. The list of targeted journalists included reporters from The Washington Post, The New York Times, and The Wall Street Journal, among others.
Political opponents: In 2019, it was reported that Pegasus had been used to target the phone of a prominent Mexican opposition leader, who was investigating corruption in the country's ruling party.
Human rights activists: In 2018, it was reported that Pegasus had been used to target a Saudi activist who had been critical of the country's government. The activist was subsequently arrested and imprisoned.
Government officials: In 2020, it was reported that Pegasus had been used to target the phones of top officials in several countries, including France, Morocco, and Lebanon. In some cases, the targets included prime ministers and heads of state.
Business leaders: In 2021, it was reported that Pegasus had been used to target the phones of several executives at the French newspaper, Le Monde, as well as executives at other French companies.
These are just a few examples of the many cases where Pegasus has been used to target individuals or groups. Its use has raised significant ethical and legal concerns, particularly in cases where it is used to target individuals who are not involved in criminal or terrorist activities.
In vigilant and proactive in protecting their digital devices and networks. At the same time, it also highlights the importance of ongoing research and innovation in the field of cyber security, in order to keep pace with new and evolving threats.
do you know a technical reference that explain thoroughly how pegasus infect its victims?
Yes, there are several technical references available that provide detailed information on how Pegasus infects its victims. Here are a few resources that you may find helpful:
Citizen Lab's technical analysis of Pegasus: Citizen Lab, a research group based at the University of Toronto, has conducted extensive research on Pegasus and its use around the world. They have published several technical reports on the spyware, including a detailed analysis of its infection vectors and command-and-control infrastructure. You can find their reports on Pegasus at the following link: https://citizenlab.ca/tag/pegasus/
Amnesty International's forensic methodology report: Amnesty International, a human rights organization, has also conducted research on Pegasus and its use by various governments around the world. They have published a forensic methodology report that provides detailed information on how they analyze infected devices to identify signs of Pegasus infection. You can find their report at the following link: https://www.amnesty.org/en/latest/research/2021/07/forensic-methodology-report-how-to-catch-nso-groups-pegasus/
Check Point's technical analysis of Pegasus: Check Point, a cybersecurity company, has also conducted a technical analysis of Pegasus and its infection methods. They have published a blog post that provides a detailed overview of how Pegasus infects its victims and how it evades detection. You can find their blog post at the following link: https://blog.checkpoint.com/2021/07/20/nso-pegasus-technical-analysis/
These resources should provide you with a thorough understanding of how Pegasus infects its victims and how it operates. However, please keep in mind that this is a rapidly evolving field and new information may become available as further research is conducted.
1. Evasion: Once Pegasus is installed on a device, it uses a number of techniques to evade detection and remain hidden. For example, it can delete its own files and logs to avoid leaving a trace, and it can disable security features on the device to make it more vulnerable.
2. Access: Once Pegasus is installed and hidden on a device, it can access almost all of the data stored on the device. It can read messages and emails, access contacts and call logs, and monitor the device's location data. It can also activate the device's camera and microphone to record audio and video and can monitor activity on social media and messaging apps.
3. Reporting: Finally, Pegasus sends the data it has collected back to the attacker's command and control (C&C) server, which is typically located outside of the target's country. The attacker can then use this data to monitor the target's activities and gain valuable intelligence.









Comments